Your Digital Maginot Line: Why Static Identity Solutions Offer a False Sense of Security
To talk about static identity protection and how it can give you a false sense of security, let’s start with a history lesson from the 1930s.
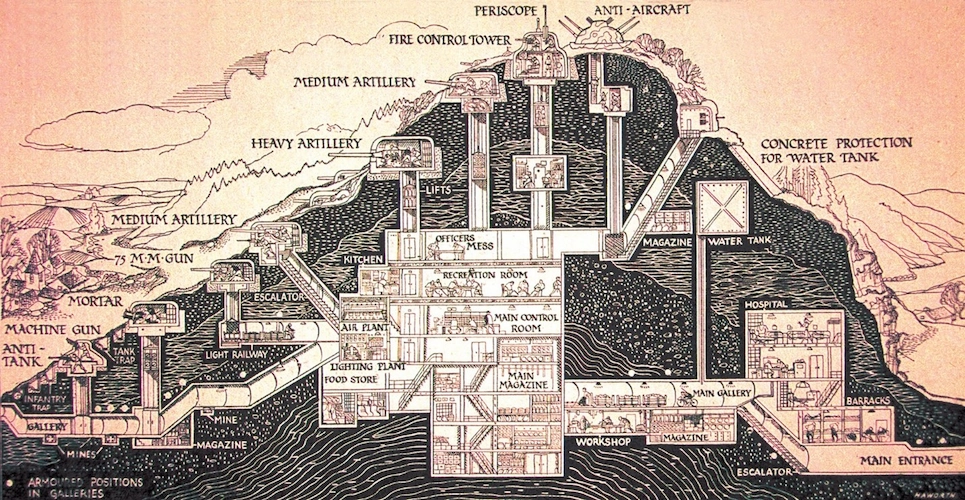
In the aftermath of World War I, and after dozens of hostile incursions from their German neighbor, the French government had had enough. After suffering significant casualties over the course of multiple conflicts, France was facing a critical shortage of manpower, both to defend the country in future conflicts. The answer, it seemed, was to build a heavily fortified wall, some 800 miles long, to keep German invaders at bay. This wall, named after French Minister of War Andre Maginot, would be known as the Maginot line.
The Maginot line was a complex series of fortifications, machine guns, mortars, and artillery connected via a vast network of tunnels, a true marvel and an impressive deterrent against future German aggression.
However.
By 1935, the Maginot line extended to protect their entire shared border with Germany, and when geopolitical tensions again started to build among their neighbors, they raced to fortify their borders with Belgium and Italy with a hodgepodge of siloed defenses. French citizens felt secure, and while improvements could still be made, it was definitely good enough, right?
Is this story starting to sound familiar?
In the end, it didn’t work out as they planned. Even with the best of intentions and with massive investments of funding and resources, their efforts to fortify their perimeter were not enough to defend against the enemy’s evolving tactics and threats. In 1940 the Germans circumvented the Maginot Line, surging forces into France by cutting through Belgium, and the rest is history.
The False Security of Your Digital Maginot Line
For years, we built our identity security like a fortress, fortified by a static set of walls, rules, and defenses designed to keep attackers out. We conducted annual access reviews, enforced strong password policies, and felt secure after passing a compliance audit. And, you could argue, for a while that was good enough.
A lot has changed since then. In today’s blink-and-you’ll-miss-it threat environment, a static defense that never evolves is like a digital Maginot Line, easily bypassed by far more sophisticated tactics.
When threats are fluid and your environment is constantly changing, you need adaptable defenses.
Four Failures of Static Identity Security
- Failure to Implement Adaptive Controls
Relying on overly broad, static permissions that don't adjust to the user's real-time context leads to access decisions based only on the user's job title. This leaves organizations vulnerable because a single compromised account can retain unnecessary access to sensitive resources.
The Solution: Modernize authorization policies using a combination of Role-Based Access Control (RBAC) and Attribute-Based Access Control (ABAC) to ensure that access decisions are dynamic and governed by prescribed rules, such as, an authenticated "HR Manager" can view salary data only if they are logging in from a corporate network during business hours.
- Failure to Maintain Continuous Identity Visibility
Like the Maginot Line, you can begin to build a unified security architecture and still end up with disconnected siloes and no way to see the bigger picture. As tech stacks become more complex and non-human identities proliferate, IT teams start to lose track of all of the identities on their network, leaving shadow identities (unmonitored API keys, service accounts) and orphaned accounts (left behind by former employees or customers with access intact) unseen and unprotected.
The Solution: Deploy full lifecycle automation and continuous discovery tools to instantly trigger deprovisioning across all systems as identity status changes (such as by retirement or termination).
- Failure to Align Security and Compliance
Some organizations treat access reviews and compliance audits as periodic, checklist-driven events, focusing on being compliant for a single day rather than being resilient every day.
The Solution: Identity Governance and Administration (IGA) integrates automated governance with security operations to provide real-time evidence of compliance and identity risk. With automation, monitoring, and control, compliance isn’t a one-time event – it’s a measurable, natural byproduct of a strong, adaptive identity program.
- Failure to Eliminate Standing Privileges
Under the Principle of Least Privilege, users should have the minimum permissions they need to do their job. When we fail to eliminate standing privilege and allow users to accumulate additional permissions as they move to new roles, without revoking their old permissions, this is what we refer to as permission creep.
The Solution: Enforce Just-in-Time (JIT) Access to eliminate all standing privileges, granting time-bound, task-specific access only when requested, and revoking it immediately after use.
Securing Both Sides of the Line with Adaptive Identity Security
The story of the Maginot Line is a powerful parable about complacency in the face of evolving threats. Today’s networks have users on both sides of the line, making your static defenses irrelevant.
The organizations that thrive in this environment will be those that build dynamic, resilient, and intelligent identity security programs fit for the reality of the modern threat landscape.
Is your IAM program ready to defend against evolving threats? Try our IAM Maturity Assessment to benchmark your program and identify opportunities for improvement.



