What is Identity & Access Management (IAM)?
Identity & Access Management (IAM) is a strategic framework of policies, processes, and technologies designed to ensure that the right human and machine identities have the appropriate level of access to the correct resources, (only what they need), at the right time (only when they need it), and for the right reasons.
What Does IAM Do?
As a subset of the broader cybersecurity discipline, IAM focuses on securing identities. In this context, identities are more than a person's name. Identities are the unique set of attributes and credentials that define who or what is attempting to access your network.
While we typically think of identity as a human construct, in the world of access management, identities can take many forms, both human and non-human.
These identities can include:
Human Identities
- Employees: Every staff member has a distinct digital identity linked to their role.
- Customers: Businesses with online portals, e-commerce sites, or apps, customer identities need protection.
- Clients: Individuals receiving services from your business may require secure access to client portals or data.
- Contractors: Non-employees who require controlled access for project work.
- Consultants: External professionals needing secure, often temporary, access to systems or information.
- Partners: External collaborators who need temporary or limited access to specific systems for joint ventures.
- Vendors: Third-party suppliers of goods or services who require secure access to specific systems.
Non-Human Identities
- Service Accounts are like user profiles for software and are used to run services or access your databases.
- SSH Keys allow your scripts to log in and deploy code securely and without the need for human intervention.
- Agentic AI: Autonomous AI systems access your network via APIs and operate with a higher level of autonomy that increases their potential risk.
- Cloud Admin Roles are highly privileged identities assigned to cloud services like Azure or AWS.
- Secrets are access credentials stored within your code or configuration files.
- API Keys & OAuth Tokens are used to facilitate seamless access between different software applications.
The fundamental premise of IAM is that every interaction with a digital resource, whether by a person, a program, or a device, originates from an identity. IAM's role within cybersecurity is to manage and protect these identities, ensuring that each user’s identity is verified, their access is appropriate, and their activities are monitored and logged.
What Does Identity & Access Management (IAM) Do?
An IAM solution is made up of a variety of tools and services designed to authenticate, authorize, audit, and govern access to your network. A modern IAM program could include:
1. Single Sign-On
Single sign-on (SSO) simplifies and secures access by allowing users to authenticate their identity and access multiple tools and services via a single login.
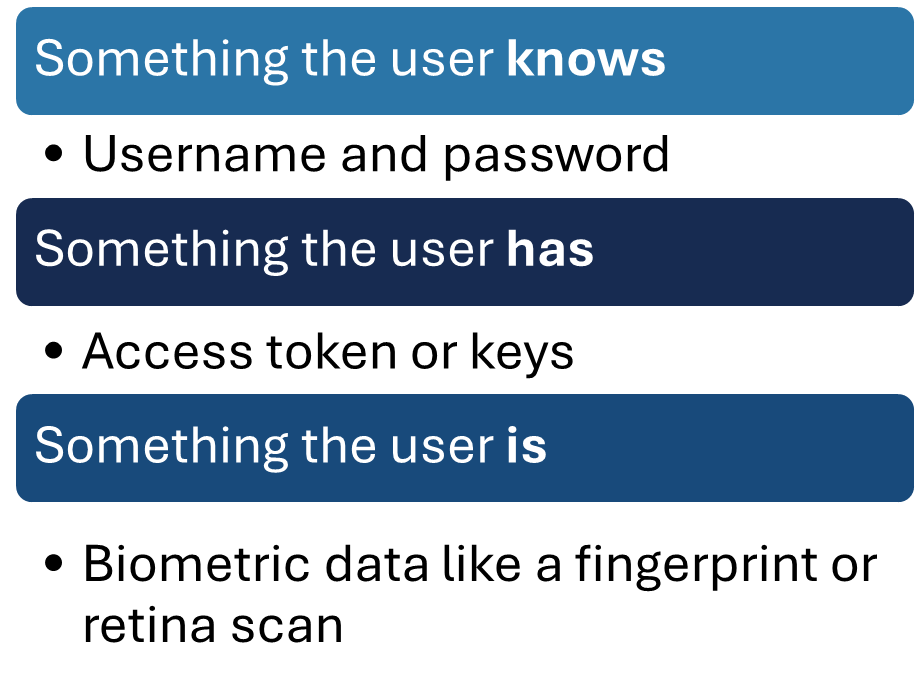
2. Multi-Factor Authentication (MFA)
According to Microsoft’s 2024 Digital Defender Report, more than 99% cyberattacks are password-based. Multi-factor authentication protects against these attacks by employing multiple authentication methods (something you know, something you have, and something you are) to fully verify a user's identity.
3. Privileged Access Management
The French philosopher Voltaire put it best, “with great power comes great responsibility.” Admins and super-admins are powerful identities that need powerful oversight and protection. As part of your comprehensive IAM program, Privileged Access Management (PAM) is designed to secure access to your most privileged accounts, providing granular access controls and detailed audit trails.
4. Identity Fabric
The larger the organization, the more complex the tech stack. IAM offers a blanket of protection to secure access for your human users, both remote and on-prem, and non-human users like APIs, service accounts, AI agents, and cloud services.
5. Zero Trust/Least Privilege
Over-privileged accounts are a significant vulnerability. IAM implements zero-trust and least privilege policies with rigorous enforcement of Role-Based Access Controls (RBAC) or Account-Based Access Controls (ABAC), which limit access to what is needed by that identity, at that time.
6. Identity Governance and Administration (IGA)
Identity Governance and Administration (IGA) provides comprehensive oversight over your IAM program. It ensures that all access rights are provisioned correctly, and that they are appropriate for the user’s role, compliant with privacy regulations, and are regularly reviewed. This comprehensive oversight delivers the transparency and accountability needed for compliance audits and to protect customer trust.
Who is IAM For?
- Businesses That Have Employees: As soon as you have more than a handful of staff members, efficient management of individual user accounts, passwords, and access permissions across numerous applications becomes unwieldy, and consequently, important details fall through the cracks.
- Businesses That Handle Sensitive Data: Any business that collects, processes, or stores sensitive information requires robust Identity & Access Management to meet compliance requirements and protect their users.
- Businesses Using Cloud Services: Cloud computing is a fact of life in modern business, with organizations of all sizes relying on cloud-based applications like Salesforce, Microsoft 365, Google Workspace to manage their daily workflows. These services also require strong identity security to mitigate third-party risks.
- Businesses with Remote Workers: Remote workers access company resources from various locations and require flexible yet highly secure access solutions. IAM is crucial to ensure secure access from anywhere, at any time.
- Businesses Working with Third Parties: Many organizations work with external entities such as contractors, consultants, vendors, suppliers, and other business partners. These third parties often require temporary or specific access to internal systems, data, or applications to perform their work. Securing access for third-party entities requires granular control and governance.
To put it simply: If your organization uses computers, software, or the internet, you need Identity & Access Management.
What are the Benefits of IAM?
Implementing a robust Identity & Access Management (IAM) framework is a strategic investment that fortifies defenses, improves efficiency, and ensures compliance.
Here are some of the benefits you can expect from IAM:
- Shrink Your Attack Surface: By rigorously verifying digital identities and enforcing the principle of least privilege, IAM dramatically shrinks an organization's attack surface.
- Streamline Operations: IAM automates the entire user lifecycle management, from quickly granting new employees necessary access on day one (efficient onboarding) to instantly revoking permissions when someone leaves (secure offboarding). This frees up valuable IT resources to focus on strategic initiatives rather than time-consuming administrative tasks.
- Simplify Regulatory Compliance & Audit Readiness: IAM provides the detailed audit trails and access logs necessary to demonstrate adherence to industry regulations and data privacy laws (like HIPAA, GDPR, SOC 2, PCI DSS). simplifies compliance reporting, helping organizations avoid hefty fines and legal repercussions by proving their due diligence in protecting information.
- Overcome Password Fatigue: Single Sign-On (SSO), a cornerstone of IAM, allows users to log in once and gain seamless access to all authorized applications. Simplified, secure login via SSO is more convenient for users and significantly improves overall employee productivity and satisfaction.
- Mitigate Insider Threats: IAM reduces the risk of insider threats—whether malicious or accidental by ensuring that employee access is always aligned with their current role and responsibilities. Privileged Access Management (PAM) further tightens controls on high-risk administrative accounts, which are often targets for misuse.
- Protect Your Cloud & Hybrid Environments: As businesses increasingly adopt cloud services (SaaS, IaaS) and operate across hybrid infrastructures, IAM becomes the central control plane for securing access across these distributed environments. Modern IAM ensures consistent access policies are applied whether your data resides on-premises or in multiple cloud platforms.
- Secure Third-Party Access: IAM enables secure yet efficient external collaboration by granting precise, time-limited access to third parties. Just-in-Time access minimizes exposure by ensuring external users can only access the resources you deem necessary, for AS LONG as they are necessary.



