What is Security Information and Event Management (SIEM)?
Security Information and Event Management (SIEM) is a powerful cybersecurity solution that provides a centralized, real-time view of your organization's IT security. As a critical component of a robust Identity & Access Management (IAM) program, a SIEM tool works by collecting and aggregating log data from various sources across your network. It then analyzes this data to identify potential threats, generate alerts, and log events for compliance and auditing purposes.
A SIEM system combines two key functions:
- Security Information Management (SIM): Handles long-term log storage and data analysis for forensic investigation.
- Security Event Management (SEM): Focuses on real-time monitoring and alerting for active security threats.
By integrating these capabilities, a SIEM system acts as a central command center for your security operations. It analyzes data to spot trends, detect anomalies, and generate alerts for any activity that could signify a security incident.
Who Needs a SIEM Solution?
A SIEM solution is essential for any organization serious about protecting its digital assets, but it's particularly critical for:
- Security Analysts and SOC Teams: As the primary users, analysts and SOC teams rely on SIEM dashboards and alerts to monitor the network, investigate threats, and manage incident response.
- IT Administrators: They use SIEM to monitor system health, track user activity, and troubleshoot operational issues that may have security implications.
- Compliance and Audit Officers: For organizations subject to regulations like GDPR, CCPA, FERPA, and HIPAA, SIEM provides a verifiable, tamper-proof audit trail for simplified compliance reporting.
- Businesses of All Sizes: Modern cloud-based and managed SIEM options make this powerful technology accessible to small and medium-sized businesses (SMBs) looking to enhance their cybersecurity defenses.
What Does a SIEM System Do? Key Functions Explained
A SIEM system performs several critical functions to fortify an organization's security architecture.
- Log Aggregation and Management: The core of any SIEM is its ability to collect and manage vast amounts of log data from a wide array of sources. This centralization prevents critical security information from being siloed and overlooked.
- Event Correlation: SIEM uses advanced rules and statistical analysis to connect the dots between seemingly unrelated events. For example, it can correlate a failed login attempt with a firewall alert and a malware detection event to identify a coordinated cyberattack.
- Real-Time Threat Detection and Alerting: SIEM continuously monitors event data for patterns that match predefined rules or deviate from established baselines. When a potential threat is detected, it generates an immediate alert for the security team to investigate.
- Security Incident Response: By providing detailed, context-rich information about a security event, SIEM platforms streamline the incident response process so analysts can quickly understand the scope of an attack and contain the threat.
- Compliance and Reporting: SIEM systems come with pre-built reporting templates for major regulatory frameworks to simplify audits and help organizations demonstrate compliance.
How SIEM Integrates with Your IAM Security Architecture
While distinct tools, SIEM and Identity and Access Management (IAM) are highly complementary pillars of a robust cybersecurity strategy. While IAM controls who can access resources, SIEM monitors how that access is being used.
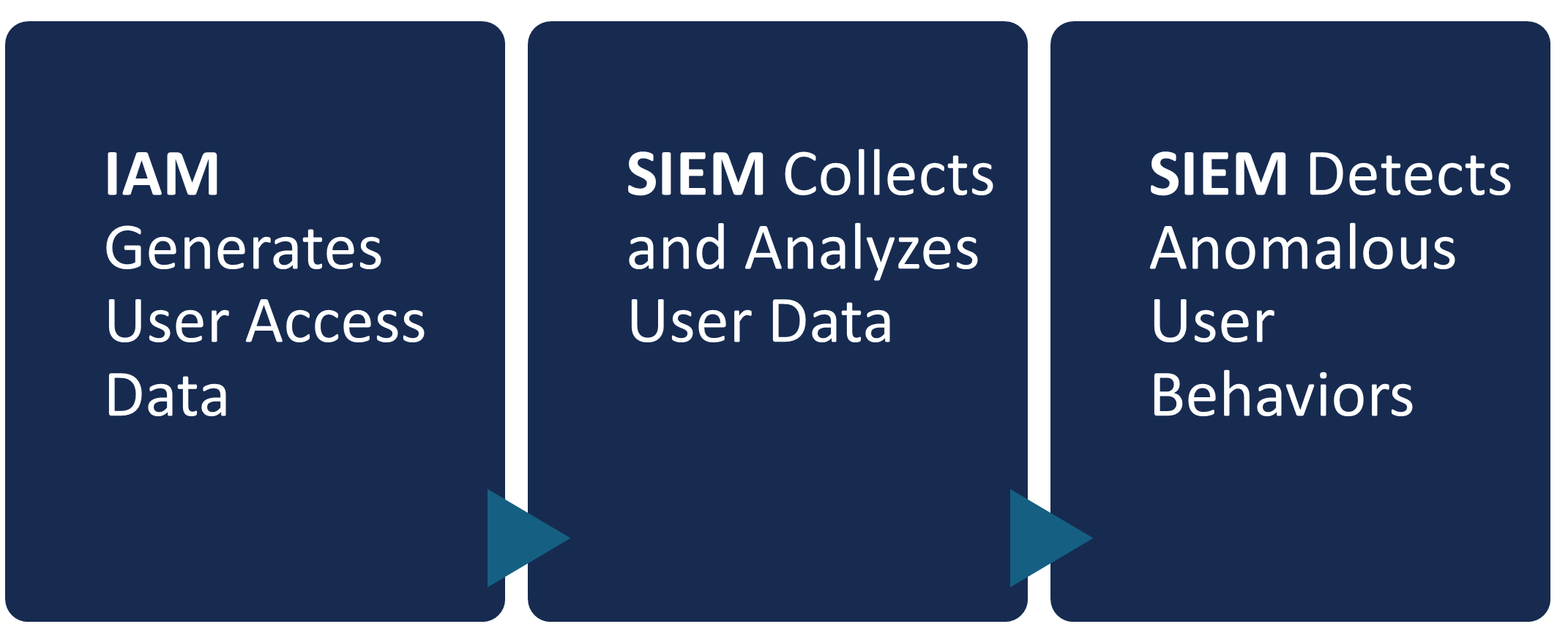
- IAM Generates User Access Data: Your IAM solution generates a rich stream of data about user authentications, access requests, and permission changes.
- SIEM Consumes and Analyzes IAM Data: The SIEM system collects logs from IAM tools and uses this identity context to enrich other security data.
- Detecting Anomalous Behavior: By analyzing IAM logs, the SIEM can detect suspicious user behavior. For example, it can flag impossible travel scenarios (a user logging in from two distant locations at once) or a user accessing sensitive data outside of normal business hours.
Integrating SIEM with your IAM architecture provides crucial context to security events, helping you answer not just "what happened?" but also "who did it?".
Key Benefits of a SIEM Solution
Implementing a SIEM solution offers significant advantages that strengthen an organization's overall security posture.
- Improved Threat Detection and Response: SIEM centralizes and correlates security data to enable faster threat identification and response, significantly reducing your Mean Time to Detect (MTTD) and Mean Time to Respond (MTTR).
- Enhanced Security Visibility: SIEM provides a "single pane of glass" for security monitoring, giving you complete visibility across your on-premises, cloud, and hybrid infrastructures.
- Streamlined Compliance and Auditing: Automating data collection and reporting makes it much easier to meet regulatory standards and simplifies the entire audit process.
- Increased Operational Efficiency: A SIEM automates many manual monitoring tasks, freeing up security analysts to focus on high-priority investigations and strategic initiatives.
- Centralized Log Management: Securely collecting and storing logs in one place is essential for both real-time security analysis and future forensic investigations.
Leveraging SIEM helps organizations move beyond basic perimeter defense and build a more intelligent, proactive, and resilient security framework.



