Shift Happens: How to Shift from a Reactive to a Proactive Identity Security Posture
It’s a whole new world. We used to be able to keep our assets confined behind the walls of our perimeter, but now our users are mobile, accessing our data from smart phones, tablets, and computers at home and abroad – from trusted home networks whose security may have deficiencies or insecure public networks at cafes and airports. In this new world, identity is your true security perimeter, which makes credential management and access protocols your new defensive line.
With no physical walls to breach, attackers have shifted their own tactics. Today, many cyberattacks aren’t the result of brute force, they are the result of compromised credentials. In fact, according to Microsoft’s 2024 Digital Defense Report, more than 99% of identity-based attacks are password-based. With so many users accessing your networks from so many places, a reactive security posture—waiting for a breach to happen, hoping you catch it in time, and then responding—is a recipe for disaster.
There really is no going back now. The rules have changed and so must we.
Let’s talk about how we can shift from a reactive stance that is always a step behind to a proactive defense that can anticipate and neutralize identity-based threats.
Shift + Perspective: From Perimeter to People

The first step is to shift your perspective. For decades, security was visualized as a castle with a moat, where the network perimeter was the primary line of defense. That worked well for physical networks, but this old security model is obsolete. Today’s reality is that with cloud applications, remote work, and interconnected devices, there is no single perimeter to defend, making identity the new perimeter.
Now that our castle’s assets can be accessed anywhere and everywhere, every user, whether human or machine, has become a potential attack vector.
A proactive approach to this new threat environment means recognizing that identities are the battleground where battles for security are won or lost. This perspective reframes every security decision. Instead of wondering if we need to build higher walls around our castle, we now must reckon with a new question: "Is this user’s identity verified, and should it have access to this resource?"
This simple but powerful mindset shift lays the groundwork for a more resilient and identity-centric security model.
Shift + Control: Embracing Zero Trust Principles
Now that we have shifted our perspective, we need to rethink how we control access. A proactive identity strategy is built on the foundation of Zero Trust, which is a security principle built on multi-factor authentication, the least privilege principle, and just-in-time access controls. Zero Trust’s core principle of "never trust, always verify" must be applied to every identity and access request, regardless of whether the user is human or machine, or where it originates. This shift in how we think about control is a significant departure from a reactive model that implicitly trusts users once they are inside the network – even when their context changes.
So what steps can we take to move toward a proactive Zero Trust security posture?
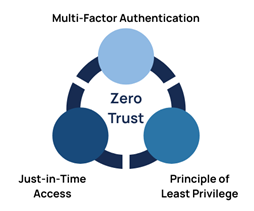
Enforce Multi-Factor Authentication (MFA): Go beyond basic passwords. Implement strong, phishing-resistant MFA across all applications and systems to create a critical verification layer.
- Implement the Principle of Least Privilege Access: Grant users the minimum level of access necessary to perform their jobs. The Principle of Least Privilege drastically reduces the potential attack surface if an account is compromised.
- Leverage Just-in-Time (JIT) Access: Eliminate standing privileges with Just-in-Time access, which grants temporary, time-bound access to sensitive resources only when needed. This minimizes the window of opportunity for attackers to exploit elevated permissions.
Shift + Visibility: Unifying Identity Data Behind a Single Pane of Glass

The next step is shifting your visibility. You can't protect what you can't see. A reactive organization often operates with fragmented identity data that is spread across dozens of disconnected systems, from Active Directory and cloud platforms to SaaS applications. This fragmentation creates blind spots that attackers can easily exploit.
To truly shift from a reactive to a proactive security posture, you must create a unified view of every identity, including its entitlements, access patterns, and activities, so you can set a baseline for normal user behavior. This visibility, which is the core of Identity Threat Detection and Response (ITDR), uses that baseline to detect and respond to potentially nefarious access attempts.
So, what does that look like? This could include a user logging in from an unusual location or accessing sensitive data for the first time. When this behavior is detected, your system can flag it as a potential threat in real-time, essentially turning your raw data into actionable security intelligence, so you can spot and stop attacks before they escalate.
Shift + Automation: Scaling Proactive Defense
The next step is to shift to automation. In a complex enterprise environment, manually managing thousands of identities and their permissions efficiently is an impossible task. To achieve a truly proactive identity security program requires automation.
Moving beyond manual processing of provisioning/de-provisioning requests and tedious access reviews, a proactive strategy leverages automation for efficiency and scalability.
- Identity Lifecycle Management: Automating onboarding, role changes, and offboarding processes ensures that a user’s access rights are always aligned with their current role and access requirements. Automation closes critical security gaps efficiently, preventing privilege escalation and the possibility of abandoned accounts that can lurk undetected on your network after an employee departs.
- Automated Access Reviews: Moving beyond tedious quarterly spreadsheets, automated tools conduct continuous access certifications. This ensures that user permissions are constantly validated.
- Immediate Threat Response: When a threat is detected, automated workflows can respond instantly by disabling an account, forcing a password reset, or notifying the security team. This automated detection and response reduces response times from hours to seconds, effectively containing threats before significant damage can occur.
Shift Forward with KeyData Cyber
If you’re ready to transition from a slow, manual, reactive security posture to a proactive identity security program that is scalable and affordable, reach out to KeyData Cyber today to schedule a complimentary workshop. We provide an in-depth analysis of your current security program and provide you with a roadmap to a more secure future.



