What is Identity Security?
Identity Security is a broad term to describe a framework of policies and technologies that ensure the right users and machines have the correct access to the right resources at the right time. It sounds a bit obscure, but if we look at it through the lens of physical security, it makes perfect sense.
Think about how you would secure a physical office building: you need a keycard to prove your identity so you can get access to the building, and that keycard will only open the doors inside the building that you're allowed to enter. It's a simple, effective system.
Identity security applies this same principle to your digital property, which includes your cloud apps, company data, and online tools. Identity & Access Management (IAM) issues and manages access via digital keycards, controls which "doors" they open, and provides oversight to ensure that a compromised credential can't be used to break into your most valued assets.
What We Mean by Identity
In the context of cybersecurity, “identity" refers to much more than just human employees. In fact, with the proliferation of IoT devices, cloud-based services, and AI agents, most identities on today’s networks are actually non-human identities, also known as machine identities.
And yet, even as these machine identities grow in number, many IT security teams are still focused almost entirely on protecting human identities, leaving dozens of unmonitored access points. The truth is, identity security must manage and protect every entity, human and non-human, as though they are a potential entry point for an attacker – because they are.
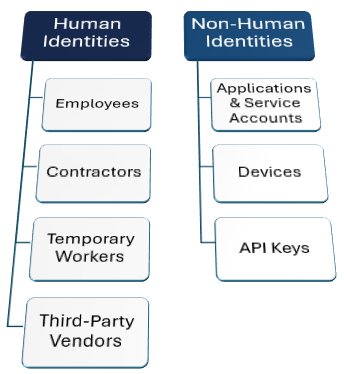
Human Identity Security
Aside from employees or customers, organizations also grant access privileges to contractors, temporary workers, and third-party vendors. Managing identity security for contractors, temporary workers, and third-party vendors is fundamentally riskier than for employees or customers because the organization has less direct control and oversight.
Non-employees tend to bring their own devices (BYOD), significantly increasing the security risks. And, since these users often fall outside of the traditional identity lifecycle, they operate outside of the formal HR system. Contractor access is often provisioned quickly with excessive privileges but is revoked slowly or forgotten when the contract ends, leading to dangerous orphaned accounts with widespread over-privileged access.
Non-Human Identity Security
As mentioned before, non-human identities now outnumber human identities on most networks. Non-human identities include:
- Applications & Service Accounts are used by software (e.g., an accounting app) to automatically communicate and pull data from other systems.
- Devices are identities too. Identity security forces every server, laptop, smartphone, and smart IoT device to prove it is legitimate and secure before being allowed on the network.
- API Keys are another type of identity. These powerful, automated "passwords" are used by various cloud services to link up and exchange data over Application Programming Interfaces (APIs).
The Three Core Pillars of Identity Security

Authentication
Authentication occurs at sign-in. While a username and password used to be enough, strong authentication today requires Multi-Factor Authentication (MFA), which makes users prove their identity in more than one way, typically combining two or more of the following:
- Something you know (a password)
- Something you have (a code from your phone app or physical key)
- Something you are (a fingerprint or face scan)
By requiring multiple factors to authenticate the user, MFA makes it exponentially harder for a criminal with a stolen password to gain entry.
Authorization
Once a user or machine is authenticated, identity security dictates which resources they can access. This authorization is governed by the Principle of Least Privilege, which means giving every identity the absolute minimum level of access necessary to do its job – and no more. Placing constraints on access dramatically reduces risk by limiting the blast radius of a breach.
Governance
Governance is the administrative and oversight layer. Identity Governance and Administration (IGA) tools help automate the process of granting, reviewing, updating, and revoking access. IGA ensures that permissions are granted correctly, reviewed regularly, and revoked promptly when an employee or machine no longer needs access.
Core Disciplines of Identity Security
Identity Security isn’t a single service or tool. It is a holistic strategy for protecting all digital identities—human and machine—and their associated access rights. This expansive field is built upon several integrated, specialized disciplines.
Workforce Identity & Access Management (WIAM)
Workforce Identity and Access Management (WIAM) manages the identities of your workforce, including employees, temporary workers, and contractors. It often integrates with HR systems for smooth onboarding and offboarding (Joiner-Mover-Leaver, or JML) and includes:
- Access Management (AM)verifies a user's identity (Authentication) and determines what they are allowed to do (Authorization). Key components of Access Management include Single Sign-On (SSO), Multi-Factor Authentication (MFA), and Role-Based Access Control (RBAC).
- Identity Governance and Administration (IGA) is responsible for automating access requests, user provisioning/de-provisioning, and regular access certifications (or re-certifications) to ensure users and machines only retain the privileges strictly necessary for their current role, often enforcing Segregation of Duties (SoD) policies.
- Privileged Access Management (PAM) secures the highest-risk identities—privileged accounts—which include system administrators, root accounts, and service accounts. PAM protects these powerful credentials by centralizing them and implementing Just-in-Time (JIT) access, monitoring sessions, and enforcing the Principle of Least Privilege to limit access and risk.
Customer Identity & Access Management (CIAM)
CIAM focuses on securing external user access to customer-facing applications and services by prioritizing user experience (e.g., social login, self-service) while managing consent and regulatory compliance (e.g., GDPR).
- Authentication is the process of verifying a customer's identity, evolving beyond simple passwords to reduce friction while increasing security. This is achieved through:
- Multi-Factor Authentication (MFA) that requires at least two verification methods (like a password plus a one-time code) to prevent credential theft
- Social and Third-Party Login, which allows customers to use pre-existing, trusted accounts (like Google or Apple) for faster onboarding and higher conversion
- Passwordless Authentication that utilizes modern standards like biometrics or magic links
- User Experience Design (UXD) ensures a secure, seamless experience for your customers through features like self-service management to empower customers to register, manage their profiles, update preferences, and perform password resets independently, and seamless customer journeys that maintain consistent, low-friction login and registration workflows across all digital channels (web, mobile, etc.).
- Fraud Detection involves leveraging real-time analytics and risk signals to proactively identify and prevent malicious activity targeting customer accounts.
Threat Detection and Response
Identity security may also include proactive and reactive security controls that continuously monitor the identity system for attacks.
- Identity Threat Detection and Response (ITDR) uses behavioral analytics to detect anomalies, lateral movement, and privilege escalation attempts after an attacker has compromised an identity. It then provides automated and guided response capabilities, such as revoking credentials or isolating the user, to stop the attack in progress. ITDR effectively serves as the security layer for the entire identity infrastructure.
- Identity Security Posture Management (ISPM)is a continuous, preventative approach that scans all identity systems (your CIAM, WIAM, IGA, PAM, etc.) to identify and mitigate misconfigurations, configuration drift, and excessive permissions that could be exploited by an attacker, effectively reducing the overall identity attack surface.
Cloud-Native Identity Security
- Cloud Infrastructure Entitlement Management (CIEM) focuses on access and entitlements across highly complex, permissions-rich cloud platforms (like AWS, Azure, GCP), analyzing potentially billions of privileges held by human, and non-human identities to automatically enforce the Principle of Least Privilege.
- Cloud Security Posture Management (CSPM): While not purely an identity discipline, CSPM has a critical role to play. It continuously monitors cloud environments to identify general security misconfigurations, such as unencrypted storage buckets or overly permissive network firewall rules. CSPM also supports identity security by flagging misconfigurations resulting in excessive identity privileges, providing the crucial context needed to prioritize the most dangerous identity risks.
- Machine Identity Management (MIM) / Non-Human Identity (NHI) Management provides comprehensive lifecycle management for non-user identities like API keys, service accounts, code signing certificates, and secrets. Given that machine identities are often granted excessive and unmonitored privileges, MIM ensures that machine identities are properly inventoried, have time-bound access, and their credentials are automatically rotated and vaulted when they are no longer needed.



